AZG News Hub
Your go-to source for the latest news and informative articles.
Data Transfer: The Undercover Hero of Digital Connectivity
Discover the hidden power of data transfer and how it fuels our digital world! Uncover the secrets behind seamless connectivity.
How Data Transfer Works: The Backbone of Digital Communication
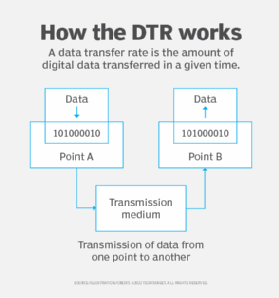
Data transfer is fundamental to our connected world, comprising the mechanisms that enable the transmission of information between devices over networks. This process involves several layers of technology, including protocols, which dictate how data is packaged, addressed, transmitted, routed, and received across various networks. From small-scale networks using local area connectivity to expansive global infrastructures like the internet, data transfer is the backbone of digital communication. Key protocols such as TCP/IP (Transmission Control Protocol/Internet Protocol) ensure that data packets reach their destination reliably, often leveraging a process called segmentation, where data is divided into manageable sections to avoid transmission errors.
Moreover, data transfer encompasses not just the technical aspects but also the various types of communication models—be it asynchronous or synchronous communication. In asynchronous modes, data can be sent without the need for both parties to be engaged simultaneously, while synchronous communication requires real-time interaction between sender and receiver. This flexibility allows businesses and individuals to choose methods that best suit their needs, leading to an ever-expanding array of applications from email and instant messaging to cloud computing and live streaming services. The efficient handling and transfer of data thus empower a myriad of digital interactions we rely on daily.
Counter-Strike is a popular series of tactical first-person shooter video games, with players split into two teams: terrorists and counter-terrorists. The game emphasizes teamwork, strategy, and skill, making it a favorite in the competitive gaming community. If you're interested in enhancing your gaming experience, check out the Top 10 usb c accessories that can improve your setup.
The Importance of Data Transfer in Today's Digital Landscape
In today's digital landscape, data transfer is a crucial component of effective communication and information exchange. With the exponential growth of digital technologies and the increasing reliance on cloud services, the ability to swiftly and securely transfer data can significantly impact a business's operational efficiency. Whether it’s sending sensitive information to clients, conducting real-time analytics, or collaborating across global teams, the importance of data transfer cannot be overstated. It ensures that relevant data reaches the intended audience promptly, thus facilitating better decision-making and enhanced productivity.
Moreover, the security of data transfer has become paramount as cyber threats evolve. Organizations must implement robust protocols to protect sensitive information during transmission, given the rising instances of data breaches. Utilizing encryption methods and secure file transfer protocols can safeguard against unauthorized access and maintain data integrity. As businesses increasingly adopt remote work models, understanding the significance of secure data transfer not only helps in compliance with regulations but also in building trust with clients and stakeholders.
What Are the Challenges of Data Transfer and How Can They Be Overcome?
The process of data transfer is crucial for businesses and individuals alike, yet it comes with a myriad of challenges. One of the primary issues is data integrity, where data can become corrupted or lost during transmission. This can occur due to various factors, such as poor network connectivity or incompatible data formats. To mitigate these risks, organizations can implement measures like encryption and use reliable protocols. Additionally, utilizing error-checking methods and ensuring compatibility with different systems can significantly enhance the process.
Another significant challenge in data transfer is maintaining security. With the rise in cyber threats, sensitive information is at heightened risk during transmission. Adopting robust security measures is essential, and businesses should consider employing technologies such as VPNs and end-to-end encryption methods to safeguard their data. Furthermore, regular training sessions for employees on best practices for handling data can help prevent human errors that often lead to breaches. By prioritizing these strategies, the challenges associated with data transfer can be effectively overcome.